Hello Guys,
In this post we are going to disscuss about the file /etc/shadow. To change the password of the user on linux system we use the command ‘passwd‘, But on /etc/passwd file we don’t find any password details of the user, rather we can find it on /etc/shadow file.
Lets dive into the file for more details,
Snippets of /etc/shadow file
hplip:*:15630:0:99999:7::: sathish:$6$GcpgrEm9$TY.skPn9zxiNN5c8LFZYQt/DmeOggy2IycFWpW.6DP8IhI90lDuPLQ6k/jd5wiE.C4TmGXZoTiSqIR3rHljHJ.:15751:0:99999:7::: libuuid:!:15630:0:99999:7:::
Syntax
The /etc/shadow has 9 fields.
User : Encrypted Password : Date of last change password : Min. password age : Max. password age : Password warning period : Password interactive period : Account expiration date : Reserved field
where as ‘ : ‘ is the field separator.
Again within the encrypted Password (2nd field) we can separate it by ‘ $ ‘
$ id $ Salt $ Actual Encrypted Password.
| Id | Hash Algorithm Name | Length |
| 1 | MD5 | 22 characters |
| 2a | Blow Fish | |
| 5 | SHA 256 (since glibc 2.7) | 43 characters |
| 6 | SHA 512 (since glibc 2.7) | 86 characters |
The ‘Salt‘ and ‘Encrypted Password’ are drawn from the set [a-z A-Z 0-9 . /]
To change the hashing algorithm, we need to change it in the file /etc/pam.d/common-password.
For the user ‘sathish‘ you can note down $ 6 $, which actually indicates that the hashing algorithm is SHA 512 and the length of encrypted password is 86 characters(note from the table).
Snapshot : 0
File Name : /etc/pam.d/common-password
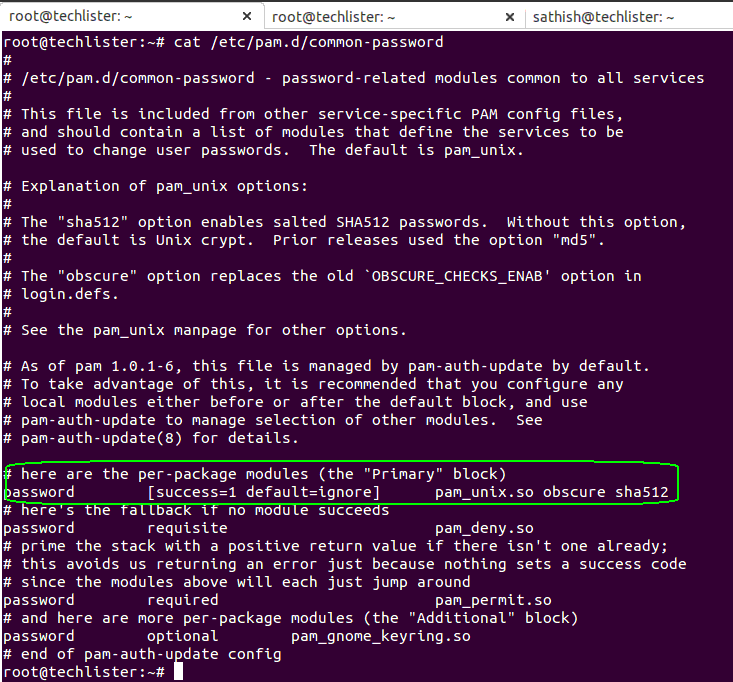
Inference :
- Green Encircled : You can note down that the hashing algorithm is ‘sha512‘ .
Snapshot : 1
Now we will be suggesting to use ‘sha256’ hashing algorithm.
Just simply edit the above line to ‘sha256’ using your favorite editor(comment the line using ‘#’).
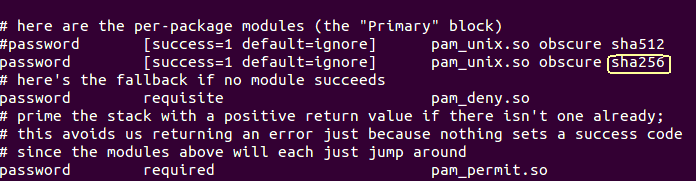
- You can note down that ‘sha256‘ is enabled now.
Snapshot : 2
Now we will check that hashing algorithm is sha256; that can be verified by creating a user.
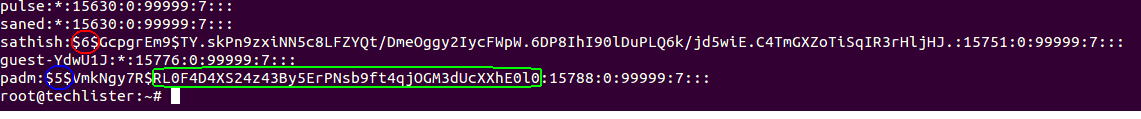
Inference :
- The blue encircled($5$) for the user padm uses the hashing algorithm sha256 based on the id 5.
- Also note that the changes have not affected the user sathish since its holding the same value ‘6’ which refers to sha512 which is of 86 characters length.
- So changes will not be affecting the existing users.
Snapshot : 3
Now we want to force all the other users to change the password, so that their hashing algorithm will change from * (anything 😉 ) to sha256 .
Now we are going to list when the password was last changed by the user.
chage -l sathish
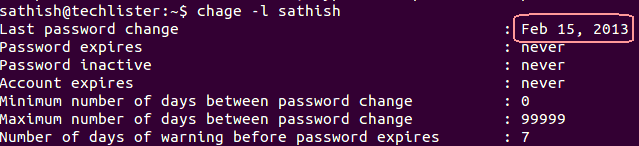
Inference :
- Password changed lastly on ‘Feb 15, 2013’
Snapshot : 4
Now we force the user ‘sathish’ to change the password. This can be done by the command as follows
chage -d 0 sathish
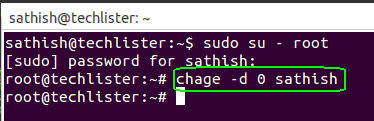
Snapshot : 5
On the next successful login of the user ‘sathish’, system will prompt the user to change the password.
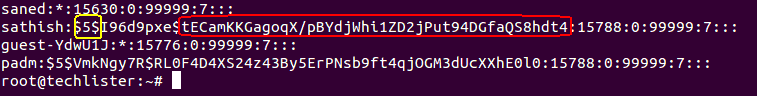
Inference :
- Yellow encircled : 5 refers => hashing algorithm sha256.
- Red Encircled : Encrypted password length is 43 characters.
Snapshot : 6
Lets verify when is the password changed for the user sathish recently.
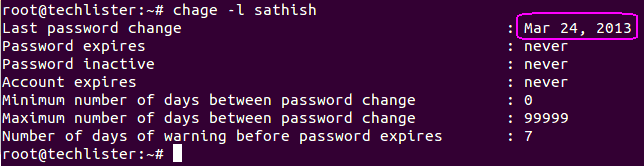
Summary :
- /etc/shadow file contains the information about password, like hashing algorithm, password expiry, interactive and so on.
- /etc/pam.d/common-password password related modules in this file we can specify which hashing algorithm to use.
- chage -l <<user>> is list when the password has been changed recently.
- chage -d 0 <<user>> is used to change the password forcibly.
Everything in linux is file, Learn more about files. 🙂 😉